RFID Solutions for Access Control
Most organizations today require a performing and efficient access control system. There are many reasons for having such a system and these include:
1) Enhanced security to limit access to restricted areas,
2) Tracking employee activity,
3) Improve loss prevention and
4) Compliance to higher internal or government regulated security measures post 9-11 to name just a few.
 RFID technology is quickly becoming a popular choice since the advancement in technology makes a variety of solutions available to any organization.
RFID technology is quickly becoming a popular choice since the advancement in technology makes a variety of solutions available to any organization.
There are major deficiencies in the legacy solutions that use the traditional access control systems. Barcodes, magnetic stripes, and proximity readers all rely on the user to either make contact or place the badge very close to the reader. In addition, bar codes can only be read one at a time and the respective embedded information cannot be updated. Such limitations can be cumbersome and time consuming.
An RFID access control system can provide an easy and efficient solution. RFID badges can be read from much further distances than other traditional technologies and the embedded electronic information for each badge can be over-written repeatedly. The increased reading distance thus enables other tracking technologies like surveillance cameras to be activated in conjunction with an employee being in their vicinity. Furthermore, multiple RFID badges can be read all at the same time. Information about employee access, attendance, and duties performed, can be easily and efficiently monitored and stored in a database. Access information can also be tied to a Windows Active Directory or LDAP for user authentication and therefore be synchronized to an authorized access scheme..
GAO RFID Access Control Solution:
GAO RFID implements a variety of solutions that solve the access control concerns of an organization. Innovative GAO solutions will help a company improve security and make employee activity tracking an easy and efficient task. Our systems can be designed to ensure that an organization is compliant with the latest government security regulations and construct or improve the current loss prevention program. These benefits will make an immediate impact and, over time, will improve efficiency and significantly reduce or even eliminate losses.
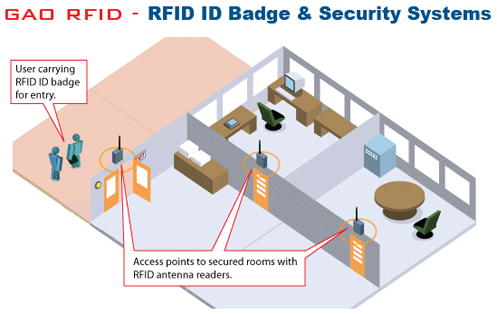
GAO RFID offers a variety of cards and readers that either fit perfectly in your organization’s environment or can be easily customized to do so. In addition, our systems are designed with employee privacy in mind, since our solutions are constructed to track only the information intended, while keeping an ethical approach to employee privacy.
What Makes Up an Access Control System?
The GAO RFID Access Control System is a modern solution that grants authorized users who carry a valid badge access to areas and equipment. The system is powered by three key components:
- GAO Access Control Software
- GAO RFID Badges/Tags
- GAO RFID Readers
These three components work together to provide access to your users, and is highly customizable to fit the requirements of every business environment. Through three simple steps, the GAO Access Control System ensures access is only granted to users who are authorized to receive it. Here’s how:
STEP 2:
GAO RFID Readers are installed at strategic points within your environment or on specific machines so that they can “read” the signals being broadcasted by the GAO RFID Tags worn by your users.
STEP 3:
Each GAO RFID Tag assigned to your users transmits data. This information is then imported into the GAO Access Control Software. Through an easy-to-use interface, you can configure access permissions and retrieve access data from a PC, remotely on your web browser, or even on a mobile device.
Access Control System Benefits
Grant Easy Access
Date & Time Stamps
Control Access Per Pass
Increase Productivity
Payroll Audit Trail
Improved Security
RFID Access Control System Details
Click on any item below to learn more
If your business is like most organizations, you will require an efficient system that enables or limits access to specialized equipment and areas within your office, warehouse, or factory; this offers safety, security, and convenience for both you and for employees.
How does Access Control ensure safety?
When you have expensive or potentially dangerous machines that can only be operated by certified and authorized personnel, Access Control is the answer. These equipment become tamperproof and access is only granted to personnel who are given permission. Different operational levels can be programmed and usage can be electronically logged to provide managers with maximum visibility.
How does Access Control provide security?
The security of people is fast becoming an important consideration in every enterprise and institution. Using Access Control, preventing unauthorized individuals from entering a building and denying access to certain personnel and visitors to sensitive areas of a building are possible, ensuring peace of mind for your employees and to your workplace.
How does Access Control offer convenience?
Speed and efficiency: together, they offer unparalleled convenience to personnel and vehicles in your business. Hands-free access eliminates long queues, while unmanned gates reduce unnecessary checks and labour. Having an automated way to control access provides convenience throughout your organization, allowing you to focus on the real tasks at hand.
Access Control answers these common questions faced by today’s businesses:
- We want to give access to sensitive zones to only authorized personnel
- We want to deter and detect possible breaches within our building
- We’re looking for a hands-free access control system that requires no user effort
- We want to promote traffic flow in a green environment by enabling vehicles to pass through our facility without congestion or long queues.
- We need a system that complies with the government regulated security measures
- We need access keys that are inexpensive to replace and difficult to copy for our warehouse equipment
- We want to control access to machines based on individual operator certifications in our company
- We’d like to keep track of our machines’ operating hours and safe usage to ensure a proper audit trail
- We are looking for a way to trigger our surveillance cameras when certain areas are accessed in our office
At GAO RFID, we have many years of experience creating RFID access controls systems for our customers to ensure safety and efficiency. While we offer customized solutions, below are the Access Control Systems we have developed and deployed for our customers:
- Learn about our Commercial Building Access Control System
- Learn about our Conference & Event Access Control System
- Learn about our Construction Site Access Control System
- Learn about our Employee Time & Attendance Access Control System
- Learn about our Hand-Free Access Control System for Institutions and Manufacturing
- Learn about our Multi-Tenant Residential Access Control System
- Learn about our Wide Area Long Range Access Control System
Want to be sure your business needs RFID Access Control? The following questions can help you to decide:
Do you need a more dependable Access Control system that doesn’t depend on frustrating, inconsistent magnetic stripe technology?
Access Control using RFID doesn’t require swiping or line of sight scanning—in some cases, it requires absolutely no user involvement at all!
Do you have specialized equipment on your shop floor which only certified, authorized employees should operate?
Access Control is not only about doors; the system can be integrated to grant access to equipment and machines, so that only authorized personnel can use them.
Does your condominium building require a solution that provides access and security to your residents?
You can limit access to the building and use of facilities to only authorized residents who carrying a programmed RFID badge. This application can even be installed in your mailbox area to allow only authorized residents access to their assigned mailboxes—free of keys!
Do you need to provide a heightened sense of security at your gated community?
Implementing RFID Access Control at your gate community provides an automated way of managing the access to the streets and neighbourhood. In addition, the system can track vehicle entries and exits, which provides valuable information in situations of theft or emergencies.
If you answered yes to any of the questions above, then GAO Access Control can enhance the safety and security of your business environment.
How RFID Applies to an Access Control System
Click on any item below to learn more
By installing RFID readers strategically throughout your work environment and assigning RFID badges to your personnel, access to sensitive areas or specialized equipment can be controlled and monitored. Unlike conventional access control systems that use bar code or magnetic stripe technology, RFID Access Control provides an easy way for users to gain access, such as simple touch and go proximity actions or a fully hands-free operation. As the system controls access to every part of your business, it is also logging usage data so that you have important information readily available for review.
An increasingly popular situation where Access Control is needed is when businesses are located in large buildings that may often house a number of different companies or departments; this is where reliable and measurable Access Control is required. With entranceways of buildings and doors on different floors secured with RFID readers, employees are given RFID badges that grant them access rights unique to their company and authorization level. This provides a reliable way to control access in shared office buildings
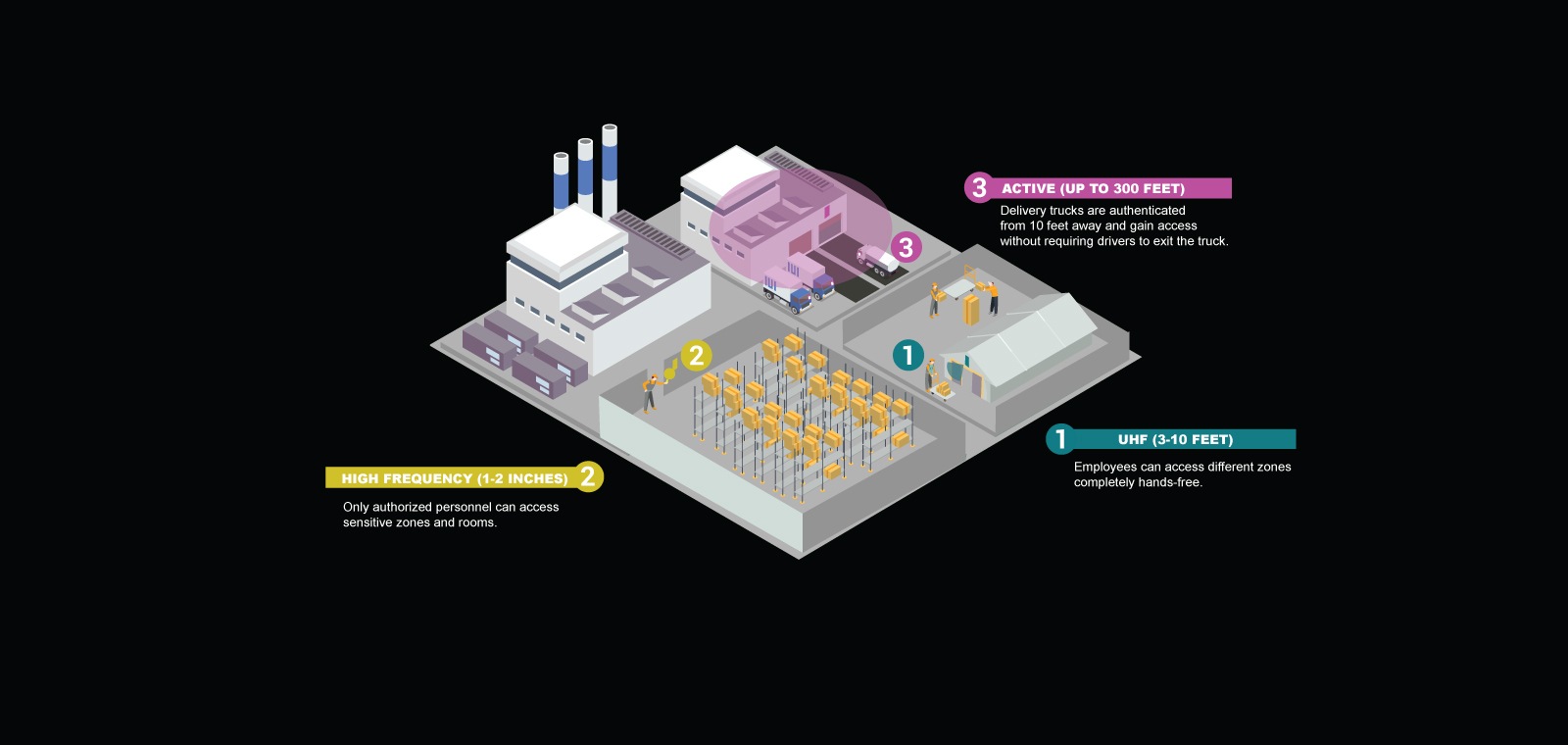
The GAO Short Range Access Control System is one of two Passive RFID versions available when you choose our Access Control System. It uses two distinct radio frequencies: low frequency and high frequency. The low frequency system uses the 125 KHz frequency, while high frequency system is based on 13.56 MHz.
The GAO Short Range Access Control System provides a near-touch reading distance of 2-6 cm. Short range access is most effective for applications where access to rooms is required, or where an operator-friendly access control for specialized machinery is needed. Using an RFID badge or key fob, personnel scan for access at close proximity. The result is an efficient, unmanned operation that ensures the control of access to the things the matter most in your business.
The Bottom Line
The GAO Short Range Access Control System lets you:
- Economically and easily expand your solution
- Control access to buildings and restricted areas
- Restrict access to dangerous machinery to only certified operators
- Log access data for detailed reporting
The GAO Mid-Range Access Control System uses Passive RFID technology, one of two passive versions available on our Access Control System. Using the Ultra-High Frequency (UHF) band of 900 MHz, the system is able to read the RFID badges or lanyards worn by personnel from up to 5 metres away—thereby providing access control to business environments that require hands-free operation. When personnel pass by a UHF Reader gate, the Reader sends signals and powers on the RFID lanyards. Information is then reflected back to the Reader, and access is granted.
The Bottom Line
The GAO Mid-Range Access Control System provides:
- Mid-range reading that does not require line of sight
- Hands-free access control
- Detailed access reporting
The GAO Long Range Access Control System is the Active RFID version of our access control solution. The system uses the 433 MHz and 2.45 Ghz bands which allows for the continuous transmission of vehicle information to RFID Receivers installed in the environment. Each vehicle is outfitted with an RFID transponder, and when they approach gated zones, access is automatically granted without requiring the driver to lean outwards to show access credentials.
Designed to support reading distances of up to 100 metres, this system can read vehicle information from long range to provide a convenient and secure way for vehicles to access any business environment. Being fully automated, this system helps promote traffic flow by helping to avoid congestion, miscommunication or unnecessary queues which greatly reduce emissions. All vehicle access data is logged and accessible via alerts and customizable reports.
Bottom Line
The GAO Long Range Access Control System helps you:
- Monitor real-time vehicle movement alerts
- Record detailed vehicle arrival and departure times
- Automated access control for heavy equipment vehicles
- Safe and secure access for fleet vehicle environments
The GAO Access Control System is available as a cloud-computing solution. Using our Cloud solution or SaaS means you have online access to the system without having to make costly investments in servers and other infrastructure. Instead, the services-based system is hosted and maintained by us and you pay for applications only when you need them.
Benefits of the Cloud or SaaS-based GAO Access Control System:
- Lower initial investment by avoiding costly infrastructure expenses
- Faster roll out for a quicker ROI
- Ongoing software updates
- Highly scalable
- Access anywhere through a web browser
- Always-on and secure with the option of hosting on our servers or your own private network
Access Control System: Applications
The GAO Access Control System has been successfully applied to the industries world-wide:
 Retail Trade & Rental Industry
Retail Trade & Rental Industry
Retail and rental businesses have unique security needs that extend beyond simply preventing theft. Access Control systems play a vital role in managing access to various areas within these establishments, enhancing security, and improving overall operational efficiency.
- Securing High-Value Inventory Areas: In retail stores, Access Control systems can be used to restrict access to high-value inventory areas such as jewelry displays, electronics sections, or luxury goods departments. This helps to deter theft and prevent unauthorized access to valuable merchandise.
- Controlling Access to Back-of-House Areas: Access Control systems can be implemented to control access to back-of-house areas such as stockrooms, employee break rooms, and administrative offices. This helps to prevent unauthorized entry and maintain a secure work environment.
- Managing Access to Cash Handling Areas: Access Control is crucial for securing cash handling areas such as registers, safes, and counting rooms. By restricting access to these areas, businesses can minimize the risk of theft and ensure the security of cash transactions.
- Controlling Access to Rental Equipment: In rental businesses, Access Control systems can be used to restrict access to rental equipment, such as vehicles, tools, and machinery. This helps to prevent unauthorized use of equipment and ensure proper inventory management.
- Securing After-Hours Access: Access Control systems can be used to manage access to the premises after business hours. This allows authorized personnel, such as security guards or maintenance staff, to access the building while restricting access to unauthorized individuals.
- Improving Employee Safety: By controlling access to different areas of the store, Access Control systems can help to improve employee safety. For example, Access Control can be used to restrict access to areas with potential hazards, such as loading docks or machinery areas, to authorized personnel only.
- Compliance with Regulations: In some cases, Access Control systems may be required to comply with industry regulations or security standards. For example, businesses that handle controlled substances may be required to implement access control measures to ensure the security of these substances.
By implementing robust Access Control systems, retail and rental businesses can enhance security, improve operational efficiency, and create a safer and more secure environment for employees and customers.
Discover GAO Access Control System solutions for the Retail Trade Industry & Rental Industry
![]()
Access Control in the Manufacturing Industry
Manufacturing facilities present unique security challenges, requiring robust Access Control systems to protect valuable assets, ensure employee safety, and maintain operational integrity.
- Securing Production Areas: Access Control systems are critical for securing production areas, including assembly lines, machine shops, and clean rooms. By restricting access to these areas, businesses can prevent unauthorized entry and protect sensitive equipment and processes.
- Controlling Access to Hazardous Areas: Access Control is essential for controlling access to hazardous areas within manufacturing facilities, such as areas containing chemicals, heavy machinery, or high-voltage equipment. This helps to prevent accidents and ensure employee safety.
- Managing Access to Restricted Areas: Access Control can be used to restrict access to restricted areas within the manufacturing facility, such as research and development labs, server rooms, or executive offices. This helps to protect sensitive information and maintain confidentiality.
- Securing Warehouse and Inventory Areas: Access Control systems are crucial for securing warehouse and inventory areas, preventing unauthorized access to raw materials, finished goods, and valuable equipment. This helps to prevent theft and maintain inventory integrity.
- Controlling Access to Maintenance Areas: Access Control can be used to restrict access to maintenance areas and equipment rooms. This helps to prevent unauthorized equipment use and ensure the safety of maintenance personnel.
- Improving Employee Safety: By controlling access to different areas of the manufacturing facility, Access Control systems can help to improve employee safety. For example, Access Control can be used to restrict access to areas with potential hazards, such as areas containing heavy machinery or hazardous chemicals.
- Compliance with Regulations: In some cases, Access Control systems may be required to comply with industry regulations or security standards. For example, manufacturing facilities that handle hazardous materials may be required to implement access control measures to ensure the safety and security of these materials.
By implementing robust Access Control systems, manufacturing businesses can enhance security, improve operational efficiency, and create a safer and more secure work environment for employees.
Discover Access Control System solutions for the Manufacturing Industry
 Building Management Industry
Building Management Industry
Modern building management demands robust and efficient security measures. RFID-powered access control systems offer a sophisticated solution, providing secure and convenient access to designated areas within a building.
How RFID Access Control Works in Building Management:
- Secure Entry: RFID readers are installed at entry points, such as doors, gates, and elevators.
- Authorized Access: Employees and authorized personnel are issued unique RFID badges or key fobs.
- Access Granted: When an authorized individual presents their RFID credential to the reader, the system verifies their identity and grants access.
- Real-time Monitoring: Access events are recorded in real-time, providing valuable data for security analysis and reporting.
- Access Control Levels: Access permissions can be customized for each individual or group, restricting access to specific areas or during certain hours.
Benefits of RFID Access Control for Building Management:
- Enhanced Security: Prevents unauthorized access to sensitive areas, improving overall building security.
- Improved Efficiency: Streamlines entry and exit processes, reducing wait times and improving staff productivity.
- Enhanced Control: Granular control over access permissions allows for precise management of who can access which areas.
- Improved Auditing: Detailed access logs provide valuable data for security audits, incident investigations, and compliance reporting.
- Increased Convenience: Hands-free access options, such as proximity readers, offer convenience and ease of use for authorized personnel.
Key Components of an RFID Access Control System:
- RFID Readers: Devices that read information from RFID tags or badges.
- RFID Tags/Badges: Small devices containing a unique identifier that is read by the reader.
- Access Control Software: Software that manages user access permissions, monitors access events, and generates reports.
Implementing RFID Access Control in Your Building:
- Needs Assessment: Evaluate your specific security needs and identify areas that require controlled access.
- System Design: Design a system that meets your specific requirements, considering factors such as the number of entry points, the level of security required, and the desired level of integration with other building systems.
- Installation and Configuration: Professional installation and configuration ensure optimal system performance and reliability.
- Training and Support: Proper training for building staff and ongoing support from your access control provider are essential for effective system operation.
By implementing an RFID-based access control system, building managers can enhance security, improve efficiency, and gain greater control over access to their facilities.
Discover GAO Access Control System solutions for the Building Management Industry
 Healthcare Industry
Healthcare Industry
Healthcare facilities require robust and secure access control systems to protect patients, staff, and valuable assets. These systems go beyond basic entry and exit points, addressing the unique needs of various departments and areas within a hospital or clinic.
Patient Areas: Access control plays a crucial role in safeguarding patient privacy and safety.
- Restricted Areas: Access to sensitive areas like intensive care units (ICUs), operating rooms (ORs), and neonatal wards is strictly controlled. Only authorized personnel, such as doctors, nurses, and designated staff, can enter these areas.
- Patient Rooms: While patient rooms may have varying levels of access, control mechanisms can ensure that only authorized individuals (doctors, nurses, family members) can enter. This enhances patient privacy and security.
- Visitor Management: Access control systems can be integrated with visitor management software to track visitors, ensure proper identification, and limit access to specific areas.
Staff Areas: Access control enhances staff security and ensures proper workflow.
- Staff Only Areas: Designated staff-only areas, such as break rooms, offices, and medication rooms, require controlled access to prevent unauthorized entry.
- Shift-Based Access: Access privileges can be easily adjusted based on staff shifts, ensuring that only authorized personnel have access during their designated working hours.
- Emergency Access: In case of emergencies, designated personnel can quickly access critical areas, such as emergency departments or secure storage areas.
Administrative Areas:
- Secure Data Centers: Access to sensitive data centers and server rooms is restricted to authorized IT personnel.
- Executive Offices: Access to executive offices and administrative areas can be controlled to maintain confidentiality and prevent unauthorized entry.
Pharmaceutical Storage:
- Controlled Substance Lockers: Secure storage areas for medications, particularly controlled substances, require strict access control. Only authorized personnel with specific credentials can access these areas.
- Inventory Management: Access control can be integrated with inventory management systems to track access to medications and other valuable supplies.
Benefits of Access Control in Healthcare:
- Enhanced Patient Safety: Protects patients from unauthorized access and potential harm.
- Improved Staff Security: Ensures a safe and secure working environment for all staff members.
- Increased Compliance: Helps meet regulatory requirements and industry standards for patient privacy and security.
- Improved Efficiency: Streamlines workflows and reduces administrative overhead.
- Enhanced Asset Protection: Protects valuable equipment and medical supplies from theft or misuse.
By implementing a robust access control system, healthcare facilities can significantly enhance security, improve efficiency, and provide a safer environment for patients and staff.
Discover GAO Access Control System solutions for the Healthcare Industry
Government & Military
Government and Military agencies operate in environments demanding thehighest levels of security. From sensitive government facilities to military bases, robust access control systems are paramount to protect personnel, assets, and national interests.
Key Considerations for Government & Military Access Control:
- High-Security Perimeter Control: Secure perimeters are critical for preventing unauthorized entry into facilities. Access control systems can integrate with various security measures, such as:
- Fences and Gates: Automated gates equipped with RFID readers grant authorized vehicles and personnel entry while denying access to unauthorized individuals.
- Guard Towers and Surveillance: Access control data can be integrated with surveillance systems to enhance situational awareness and provide real-time monitoring of entry and exit points.
- Controlled Access to Sensitive Areas:
- Restricted Areas: Access to highly sensitive areas, such as data centers, armories, and command centers, must be strictly controlled. Multi-factor authentication, including biometric verification, can be integrated with access control systems to enhance security.
- Classified Information: Access to areas containing classified information requires stringent authorization checks. Access control systems can be configured to track and audit access to these areas, ensuring compliance with security regulations.
- Visitor Management:
- Registration and Screening: Visitor management systems can be integrated with access control to track visitor movements, ensure proper registration and screening procedures, and issue temporary access credentials.
- Escort Procedures: Access control systems can be used to enforce escort procedures for visitors accessing sensitive areas, ensuring they are always accompanied by authorized personnel.
- Disaster Response and Emergency Situations:
- Evacuation Control: Access control systems can facilitate rapid evacuation during emergencies by controlling access to exit routes and monitoring the movement of personnel.
- Emergency Response Teams: Access control systems can be used to grant emergency response teams immediate access to critical areas during emergencies.
- Compliance with Regulations: Government and military agencies must adhere to strict security regulations and compliance standards. Access control systems must be designed and implemented to meet these requirements, including:
- Department of Defense (DoD) regulations: Compliance with DoD directives and standards for physical security.
- Federal Information Security Management Act (FISMA): Ensuring the security and confidentiality of government information.
Benefits of Implementing Robust Access Control:
- Enhanced Security: Protects personnel, assets, and critical infrastructure from unauthorized access and threats.
- Improved Situational Awareness: Provides real-time monitoring of entry and exit points, enhancing situational awareness and enabling rapid response to security incidents.
- Increased Operational Efficiency: Streamlines access control procedures, reducing administrative overhead and improving operational efficiency.
- Enhanced Compliance: Ensures compliance with security regulations and industry best practices.
- Improved Accountability: Tracks and audits access activity, providing valuable data for security investigations and incident response.
By implementing comprehensive access control solutions, government and military agencies can effectively secure their facilities, protect critical assets, and maintain a safe and secure operating environment.
Discover GAO Access Control System solutions for the Finance & Insurance Industry
 Information & Telecommunications Industry
Information & Telecommunications Industry
The Information & Telecommunications industry relies heavily on technology and sensitive data. Securing physical access to facilities, equipment, and data centers is critical for protecting valuable assets and maintaining business continuity.
Key Considerations for Access Control in Information & Telecommunications:
- Data Center Security:
- Restricted Access: Data centers house critical infrastructure, including servers, networking equipment, and sensitive data. Access to these areas must be strictly controlled and limited to authorized personnel.
- Multi-Factor Authentication: Implementing multi-factor authentication, such as biometric verification or two-factor authentication, enhances security for data center access.
- Physical Security Audits: Regular security audits of data centers can identify and address potential vulnerabilities in access control systems.
- Server Room Security:
- Controlled Entry: Access to server rooms should be tightly controlled to prevent unauthorized access to critical equipment.
- Environmental Monitoring: Access control systems can be integrated with environmental monitoring systems to detect and respond to potential threats such as fire, flood, or unauthorized entry.
- Remote Site Access:
- Secure Remote Access: Many organizations have remote sites, such as telecommunication towers or data centers, that require secure access.
- Remote Monitoring: Access control systems can be remotely monitored and managed, enabling proactive security measures.
- Executive Offices and Sensitive Areas:
- Controlled Access: Access to executive offices and other sensitive areas should be restricted to authorized personnel.
- Visitor Management: Implementing a robust visitor management system ensures proper registration and screening of visitors to these areas.
- Protecting Intellectual Property:
- Controlled Access to Research & Development Areas: Access to research and development areas where intellectual property is developed and stored must be tightly controlled.
- Secure Document Storage: Access control can be used to secure areas where sensitive documents and intellectual property are stored.
Benefits of Implementing Robust Access Control:
- Enhanced Data Security: Protects sensitive data and critical infrastructure from unauthorized access and threats.
- Reduced Risk of Data Breaches: Minimizes the risk of data breaches and cyberattacks resulting from physical security vulnerabilities.
- Improved Business Continuity: Ensures uninterrupted operations by maintaining the security and integrity of critical systems and data.
- Enhanced Compliance: Helps organizations comply with industry regulations and data security standards.
- Improved Operational Efficiency: Streamlines access control procedures, reducing administrative overhead and improving operational efficiency.
By implementing comprehensive access control solutions, organizations in the Information & Telecommunications industry can effectively secure their facilities, protect valuable assets, and maintain a secure and reliable operating environment.
Discover GAO Access Control System solutions for the Information & Telecommunications Industry
 Supply Chain & Logistics Industry
Supply Chain & Logistics Industry
The Supply Chain & Logistics industries encompass a vast network of interconnected operations, from warehousing and transportation to distribution and delivery. Ensuring secure and controlled access to critical areas within these operations is paramount for maintaining efficiency, protecting valuable assets, and complying with industry regulations.
Warehousing & Storage:
- Securing High-Value Goods: Access Control systems are crucial for safeguarding high-value inventory stored in warehouses. By controlling entry to specific areas, businesses can prevent unauthorized access to sensitive goods, reducing the risk of theft and pilferage.
- Controlling Access to Equipment: Access Control can be implemented to restrict the use of specialized equipment such as forklifts, loading docks, and packaging machines to authorized personnel only. This enhances safety and prevents misuse of equipment.
- Maintaining Chain of Custody: By tracking employee access to specific storage areas, Access Control systems can help maintain a clear chain of custody for goods, ensuring accountability and traceability throughout the supply chain.
Freight Trucking Services:
- Securing Vehicle Yards and Maintenance Areas: Access Control systems can be deployed to secure vehicle yards, maintenance areas, and other critical areas within trucking terminals. This helps prevent unauthorized entry and protects valuable vehicles and equipment.
- Controlling Access to Fuel Depots: Access Control can be implemented to restrict access to fuel depots and other sensitive areas within trucking terminals, preventing unauthorized fuel usage and ensuring proper fuel management.
Pipeline Transportation:
- Securing Pipeline Facilities: Access Control systems are essential for securing pipeline facilities, including compressor stations, pump stations, and control centers. By controlling access to these critical areas, businesses can prevent unauthorized entry and protect vital infrastructure.
- Controlling Access to Hazardous Areas: Access Control can be used to restrict access to hazardous areas within pipeline facilities, such as areas containing flammable gases or high-pressure equipment. This helps to enhance safety and prevent accidents.
Couriers & Messengers:
- Securing Package Handling Areas: Access Control systems can be implemented to secure package handling areas, sorting areas, and delivery docks, preventing unauthorized access to packages and ensuring the integrity of the delivery process.
- Controlling Access to Sensitive Information: Access Control can be used to restrict access to sensitive information, such as customer data and delivery schedules, within courier and messenger facilities.
Vessel Transportation:
- Securing Port and Harbor Facilities: Access Control systems are critical for securing port and harbor facilities, including docks, terminals, and control centers. By controlling access to these areas, businesses can prevent unauthorized entry and protect valuable cargo and equipment.
- Controlling Access to Restricted Areas: Access Control can be used to restrict access to restricted areas within port and harbor facilities, such as areas containing hazardous materials or sensitive equipment.
Postal Services:
- Securing Mail Processing Centers: Access Control systems can be implemented to secure mail processing centers, sorting areas, and delivery docks, preventing unauthorized access to mail and ensuring the security of postal operations.
- Controlling Access to Sensitive Areas: Access Control can be used to restrict access to sensitive areas within postal facilities, such as areas containing valuable equipment or confidential information.
General Warehousing & Storage:
- Securing Storage Areas: Access Control systems can be used to secure storage areas within warehouses, preventing unauthorized access to inventory and protecting valuable goods from theft and damage.
- Controlling Access to Equipment: Access Control can be implemented to restrict the use of specialized equipment, such as forklifts and pallet jacks, to authorized personnel only.
Refrigerated Warehousing & Storage:
- Securing Cold Storage Areas: Access Control systems are crucial for securing cold storage areas, preventing unauthorized entry and maintaining the integrity of the cold chain.
- Controlling Access to Temperature-Controlled Environments: Access Control can be used to restrict access to temperature-controlled environments, such as freezer rooms and refrigeration units, ensuring proper temperature maintenance and preventing product spoilage.
Rail Transportation:
- Securing Railway Yards and Maintenance Facilities: Access Control systems can be deployed to secure railway yards, maintenance facilities, and other critical areas within railway operations. This helps prevent unauthorized entry and protects valuable equipment and infrastructure.
- Controlling Access to Sensitive Areas: Access Control can be used to restrict access to sensitive areas within railway facilities, such as areas containing signaling equipment or high-voltage infrastructure.
By implementing robust Access Control systems, businesses within the Supply Chain & Logistics industries can enhance security, improve efficiency, and minimize risks associated with unauthorized access.
Discover GAO Access Control System solutions for the Supply Chain & Logistics Industry
 Utilities Industry
Utilities Industry
The Utilities industry operates critical infrastructure that provides essential services to communities. Securing access to facilities, equipment, and work sites is paramount for ensuring safety, reliability, and operational continuity.
Key Considerations for Access Control in the Utilities Industry:
- Substation and Power Plant Security:
- Perimeter Control: Secure perimeters around substations and power plants are essential to prevent unauthorized access and protect critical equipment.
- Controlled Access to Sensitive Areas: Access to control rooms, switchyards, and other sensitive areas must be strictly controlled and limited to authorized personnel.
- Multi-Factor Authentication: Implementing multi-factor authentication, such as biometric verification, can enhance security for access to critical areas.
- Work Site Security:
- Controlled Access to Work Zones: Access to work zones must be strictly controlled to prevent unauthorized entry and ensure the safety of personnel.
- Hot Work Permits: Access control systems can be integrated with hot work permit systems to ensure that proper safety procedures are followed before work commences in hazardous areas.
- Contractor Management: Access control systems can be used to manage access for contractors working on site, ensuring they are properly vetted and authorized to be on site.
- Remote Site Security:
- Controlled Access to Remote Sites: Access to remote sites, such as pumping stations, water treatment plants, and wind farms, must be secured to prevent vandalism, theft, and unauthorized entry.
- Remote Monitoring: Access control systems can be remotely monitored and managed, enabling proactive security measures at remote sites.
- Vehicle Access Control:
- Controlled Entry to Facilities: Access to utility facilities and work sites can be controlled for vehicles, ensuring only authorized vehicles are permitted entry.
- Vehicle Inspection: Access control systems can be integrated with vehicle inspection systems to ensure that vehicles entering the site meet safety and compliance requirements.
Benefits of Implementing Robust Access Control:
- Enhanced Safety: Protects personnel, equipment, and critical infrastructure from unauthorized access and threats.
- Improved Operational Efficiency: Streamlines access control procedures, reducing administrative overhead and improving operational efficiency.
- Reduced Risk of Incidents: Minimizes the risk of accidents, injuries, and equipment damage.
- Enhanced Compliance: Helps organizations comply with industry regulations and safety standards.
- Improved Accountability: Tracks and audits access activity, providing valuable data for incident investigations and security audits.
By implementing comprehensive access control solutions, utilities companies can effectively secure their facilities, protect critical infrastructure, and ensure the safety and reliability of essential services.
Discover GAO Access Control System solutions for the Utilities Industry
 Oil & Gas Industry
Oil & Gas Industry
The Oil & Gas industry operates in hazardous environments with significant risks. Securing access to facilities, equipment, and work sites is critical for ensuring the safety of personnel, protecting valuable assets, and preventing unauthorized entry.
Key Considerations for Access Control in the Oil & Gas Industry:
- Platform and Rig Security:
- Controlled Access: Access to offshore platforms and onshore rigs must be strictly controlled and limited to authorized personnel.
- Multi-Factor Authentication: Implementing multi-factor authentication, such as biometric verification, can enhance security for access to critical areas on offshore platforms.
- Evacuation Procedures: Access control systems can be integrated with evacuation procedures to facilitate rapid and orderly evacuation in case of emergencies.
- Pipeline and Terminal Security:
- Perimeter Security: Secure perimeters around pipelines and terminals are essential to prevent unauthorized access and sabotage.
- Controlled Access to Control Rooms: Access to control rooms and other critical areas within pipeline terminals must be tightly controlled.
- Video Surveillance Integration: Access control systems can be integrated with video surveillance systems to enhance situational awareness and provide real-time monitoring of entry and exit points.
- Work Site Security:
- Controlled Access to Work Zones: Access to work zones must be strictly controlled to prevent unauthorized entry and ensure the safety of personnel.
- Hot Work Permits: Access control systems can be integrated with hot work permit systems to ensure that proper safety procedures are followed before work commences in hazardous areas.
- Contractor Management: Access control systems can be used to manage access for contractors working on site, ensuring they are properly vetted and authorized to be on site.
- Remote Site Security:
- Controlled Access to Remote Sites: Access to remote sites, such as wellheads, pumping stations, and remote pipelines, must be secured to prevent vandalism, theft, and unauthorized entry.
- Remote Monitoring: Access control systems can be remotely monitored and managed, enabling proactive security measures at remote sites.
Benefits of Implementing Robust Access Control:
- Enhanced Safety: Protects personnel, equipment, and critical infrastructure from unauthorized access and threats.
- Reduced Risk of Incidents: Minimizes the risk of accidents, injuries, and equipment damage.
- Improved Operational Efficiency: Streamlines access control procedures, reducing administrative overhead and improving operational efficiency.
- Enhanced Compliance: Helps organizations comply with industry regulations and safety standards.
- Improved Accountability: Tracks and audits access activity, providing valuable data for incident investigations and security audits.
By implementing comprehensive access control solutions, oil and gas companies can effectively secure their facilities, protect critical infrastructure, and ensure the safety of their workforce in challenging and hazardous environments.
Discover GAO Access Control System solutions for the Oil & Gas Industry